OK, let's start with that statement above. It is a proven fact that any device connected to an IP network can suffer attacks and intrusions by hackers and viruses. And the world-installed DVRs and security cameras are on this list of devices.
Let's talk now about one of the biggest problems found in the area of CCTV, the lack of specialized technical knowledge in networks.
We can hear the statement below everywhere:
" I understand enough about networks, I know how to configure the DVR IP and ports and give my client remote access through my his phone, I also use a strong password and I change the standard access ports"
Please keep in mind that protection with password is basic and only good enough to prevent non-authorized access from non-technical people, if a hacker or virus get to your DVR, chances are that you will be in big trouble.
Arrogance is one of the biggest problems
Have you heard anyone saying that they've worked with CCTV for many years and have never had problems with DVR intrusion? Often proud of themselves and stating that only inexperienced professionals have those kind of problems.
But the truth is simple: Such arrogance can cost you a lot, because when a system of CCTV it available on the Internet, it is already at risk of invasion, no matter if you are using a strong password, different logical ports or you are using a P2P configuration from the manufacturer.
Most DVR installers do not have even 1% of a hacker knowledge. Hackers are the ones that have been studying for years to find out the best intrusion techniques to get into super complex systems. So are you sure your DVR is safe from this kind of people ?
I'm sorry to say that, but if you think like this, you are naive or arrogant.
So if you work in the CCTV area and want to learn how to improve the security of your system, keep reading this article, but keep in mind that you can not claim to be a security specialist just because you install and configure a DVR in the network, be humble, learn as much as you can.
What is the operating system of a DVR?
Linux, this is the operating system that is in the overwhelming majority of DVRs, NVRs and IP cameras on the market. Have you ever used linux?
This operating system became very famous in the IT world because it brought the possibility of being used in servers and devices developed by many manufacturers because it is a system with a central core and several other modules that can be removed to make it leaner.
So a DVR has Linux with the necessary modules operate, plus some extra programming done by the manufacturer.
==> To learn more, read the articles: How to protect your CCTV camera from Hackers and How to hack CCTV camera.
How does a CCTV system work?
Finally you will understand a little more about the working mechanism of an IP system.
See the diagram below to understand how the services work:
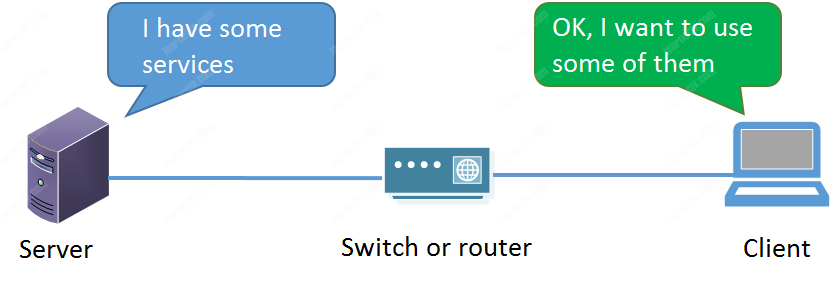
In IP network systems we consider the interaction between devices a client-server model. So, there is a server on the network that offers services and clients use them.
In CCTV, the servers can be DVRs, NVRs, recording servers, IP cameras, encoders, video analytics servers and even access control servers.
Clients are computers, laptops, cell phones, tablets, NVRs. Recording servers, access control interface, decoders, etc.
But NVRs and recording servers can be clients too?
Yes, depending on the architecture they can be servers that provide videos to computers with monitoring software or they can be clients when they are connecting to an IP camera to request streaming videos to make the recording.
What are the vulnerabilities of a network?
There are several, from the simplest to more advanced ones that can be exploited by a true hacker (called a cracker when he is an evil attacker). See the list below:
Possible attacks on a DVR, NVR or IP Camera:
- Man-in-the-middle password interception
- Brute-force attack (try a sequence of possible passwords)
- Dictionary attack (try a sequence of words as passwords)
- Exploiting vulnerability in services (such as WebServer)
- Denial of service attack (request many concurrent connections)
- Social engineering (getting information through people)
- Network scanning and use of manufacturer default passwords
- Invasion by viruses specially created for these devices
- Former technicians, employees or other people sabotaging the system
Note below an example of a very common attack used by hackers for many years, called "man-in-the-middle" where the attacker positions himself between the client and server from within the internal network or through the Internet.
When you create a password, it does not matter if it is difficult or not, it may be the longest and most complex password in the universe that it will still be displayed to the hacker.
An attack like this can be avoided by encrypting the password sent between client and server and also through secure connection via Virtual Private Network.
In brute-force attacks and dictionary attacks the hacker uses software to send a fast sequence of passwords to the DVR until find the correct one, it's just like try and error on steroids.
A software developed for this purpose can try thousands of combinations in a matter of minutes until you find the correct system password. This attack can be prevented with a password policy that combines letters, numbers and special characters.
But again keep in mind that this does not guarantee that you can have 100% security, because in the previously mentioned attack (man-in-the-middle) the attacker can get the password even if it is a hard one.
We are talking about one more step to help protect the system, combining strong password with encryption or VPN for example to reduce the risk of successful attacks.
Exploiting device services is also very common among hackers, note I'm talking about those guys who really know what they're doing, they are programmers who have software development skills and who know how to study the operating system and services that run within the camera, and video recorders.
It is possible for a hacker to buy a DVR and study the Linux modules that are available to find the vulnerabilities to make a subsequent accurate attack. This can be avoided with firmware updates created by the manufacturers, the problem lies in the fact that several of them do not pay close attention to this subject, especially the cheaper camera manufacturer brands.
There is also the issue of customers who will hardly pay for a periodic maintenance that include firmware update. Most of the time the clients have their system hacked and do not even know, because the hacker can simply log in the camera, see what they need, export the recording and leave the system quietly, he/she can even delete the LOGs of evidence.
Even major manufacturers have such vulnerability service issues, for example, the two major Chinese manufacturers had an issue called "buffer overflow" and another issue called "RTSP stream authentication" that allow administrator access to NVRs and cameras.
There are a lot of equipment already installed in homes and small businesses that have old firmware and will remain like this forever, since once installed the clients never update them.
Finally, there is the physical and social engineering issue, if people who have passwords or direct access to the systems do not care about security, an hacker can certainly exploit this failure by finding annotated passwords, talking to people or having access to logged in equipment.
There is no way to implement security that is 100%, but there are ways to reduce the risks and if you still do not have deep IT knowledge, you can at least use, safe password, use more secure and reliable equipment brands, and work on constant firmware upgrades.
A good way to convince your client about the danger of unprotected CCTV systems is show the site insecam.org where there are thousands of hacked cameras all over the world, who knows, your customer may even be on this list or about to get into it.
Go to http://www.insecam.org choose a country to check the hacked cameras around the world, and I hope you do not have any system that you have already installed available on that site.
Do not forget to share this article, please clicl the buttons below:
